Download the Citrix Workspace App
Citrix Workspace app is the easy-to-install client software that provides seamless secure access to everything you need to get work done.
USE CASE
Nearly every enterprise supplements its workforce with third-party contractors, consultants, and outsourcers, who use devices not managed by you. At the same time, many organizations are considering the cost-savings and employee benefits of a BYOD policy. How do you enable these initiatives without inflating costs, creating security and compliance issues, and creating a PC management nightmare? A lack of insight into the health of these devices creates significant risk—especially when people use them to access and store sensitive information. If attackers manage to infect them with malware, your risk of data exfiltration runs high. You also need to be able to protect every kind of operating system, considering that almost 70% of global mobile users use Android and nearly 58% of North American users use iOS1. You need a way to provide secure access to IT-sanctioned apps on a variety of operating systems while keeping unauthorized users at bay.
BENEFITS
The nature of virtual apps and desktops is to take resources off of devices themselves and deliver them from any data center or cloud, thus keeping all the associated data and intellectual property under centralized control. With the Citrix platform, your apps and desktops are device-agnostic by design. The Citrix app offers a single location for employees to securely access their apps and desktops from anywhere on any device. As user’s needs or roles change, IT can easily or even automatically provision new access and apps. Once those employees no longer need access, IT can revoke access to the app and leave no data behind on the endpoint.
BYOD can be great for productivity: 67% of employees use personal devices at work, and 69% of IT decision-makers say BYOD is a good thing2. However, unmanaged devices can allow attackers to distribute dangerous malware that can infect your entire corporate network. Citrix App Protection protects against keylogger and screen capturing malware within the Citrix app and applies enhanced security controls using Citrix Enterprise Browser® or Citrix Remote Browser Isolation® technology - even before a user logs in.
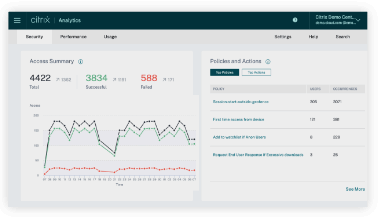
More of the world’s employees are working remotely than ever before, on a variety of devices. You need a solution that protects every kind of device and every kind of OS on the market. Citrix Secure Private Access™ can check and see if a device is managed or unmanaged and evaluate the user’s location and risk score. Your admin can then define how they want to authenticate and authorize access to apps based on these results. For example, employees may have full access to all applications when on site, but once they leave they’ll have limited access to data and applications.
With a traditional VPN, all end user devices connect directly to the network, and exposing your corporate network to unmanaged devices increases your attack surface and risk of data loss. Citrix offers a way around this challenge by providing secure access to IT-sanctioned apps, minus the need for a corporate network connection, on any device. Access is adapted based on device posture and risk factors. For employees who use the Citrix Enterprise Brower, nothing is stored on the endpoint itself, so there’s far less risk if a BYOD device is lost, stolen, or infiltrated by a bad actor.
OTHER SOLUTIONS
Deliver zero trust application access to all IT-sanctioned apps without a VPN.
Short description of product: Ensure access to all browser-based applications to help users stay productive while mitigating insider and external threats
Deliver secure virtual apps and desktops to any device.
RESOURCES



Learn from experts, gain insight from fellow users, and contribute to knowledge on Citrix technologies and integrations for more successful Citrix deployments.