Download the Citrix Workspace App
Citrix Workspace app is the easy-to-install client software that provides seamless secure access to everything you need to get work done.
USE CASE
Per Gartner, the number one cybersecurity trend last year was an expanding attack surface, a trend which has escalated with the increase in flexible work1. With more workers accessing business data from home, more employees are using personal devices for work and work devices for personal use. Employees are still the weakest link when it comes to security, according to the Cybersecurity and Security Infrastructure Agency, 84 percent of employees fell for a malicious email within the first 10 minutes of receiving it2.
While keeping your proprietary data safe is a priority, your employees also need to access that data from anywhere, on any device, so you need a solution that keeps your data secure without compromising the employee experience.
BENEFITS
Citrix app and desktop virtualization is built for secure remote work. With centralized management and built-in policy controls from NetScaler®, you can add an extra layer of security to keep data protected anywhere. This way, employees have seamless access to Windows, Linux, web and SaaS apps, while you keep threats away from your network.
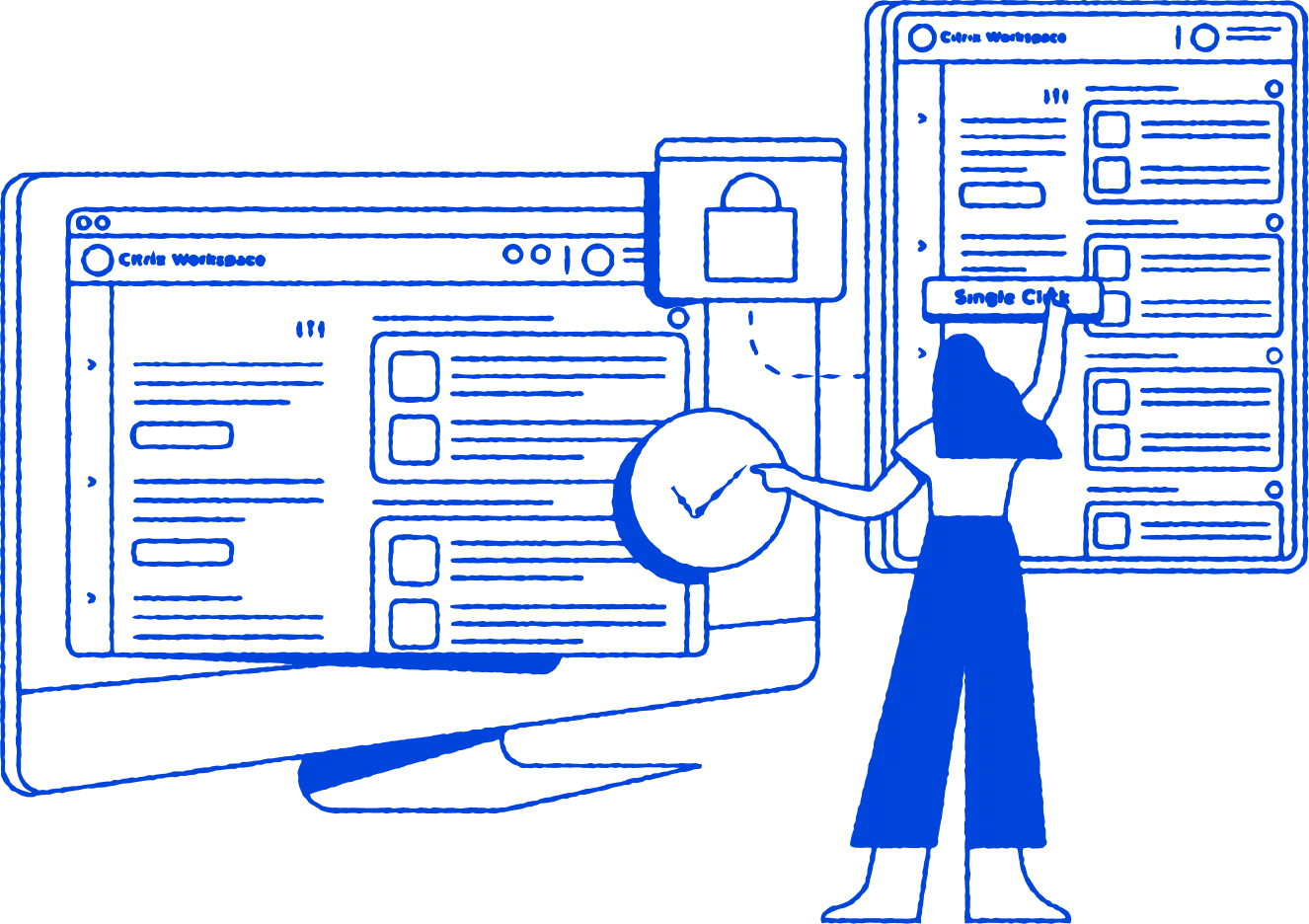
Flexible work has officially gone mainstream. That means more users are working on networks IT can’t secure, with devices that aren’t managed—a big risk for companies that rely on network-centric solutions like traditional VPNs. Using VPNs isn’t as secure as many think, since 57% of cyber attacks happened on a VPN 20223. The Citrix platform comes with Zero Trust security features for web and SaaS app access that allow admins to apply security controls based on user risk scores, locations, and device posture, and to efficiently deliver modern web apps via the Citrix app or Enterprise Browser. The Enterprise Browser — Citrix Secure Access with Chrome Enterprise — functions just like a consumer browser, but with more security controls so your users have a seamless experience without compromising on security.
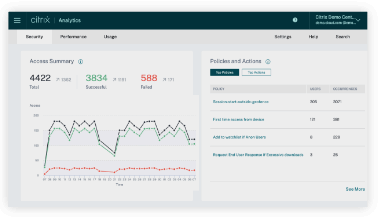
As employees work from more locations, and as apps move to the cloud, the potential for compromised data is everywhere. And with the average cost of a breach at an all-time high of $4.45 million, you can’t afford to overlook a single threat4. The Citrix platform collects user behavior data that lets you identify and automatically respond to suspicious activity. With a personalized risk score assigned to each user based on behavior, you can stay ahead of both internal and external threats long before they lead to data breaches.
Whether you want to stay ahead of the latest regulations or need to meet strict industry standards for data storage, Citrix solutions have you covered. You can use Adaptive Authentication to verify device posture to determine who gets access to what based on job roles, locations, devices, and more. You can lock down confidential customer and business data when a mobile device leaves the job site. Or you might decide to turn off specific features, such as copying and pasting, based on compliance checks throughout each session. You can even record the on-screen activity of any user session, over any type of connection, to monitor as needed based on industry requirements with Citrix Session Recording. These and other security features from Citrix make it remarkably easy for companies to meet even the toughest requirements including HIPAA, PCI, CIPAA, FIPS, and GDPR.
OTHER SOLUTIONS
Deliver secure virtual apps and desktops to any device.
Deliver zero trust application access to all IT-sanctioned apps without a VPN.
Increase security and improve end-to-end visibility, without compromising user experience.
MORE TO EXPLORE
See how Citrix DaaS™ can help you build a comprehensive and secure digital workspace

Learn from experts, gain insight from fellow users, and contribute to knowledge on Citrix technologies and integrations for more successful Citrix deployments.