Download the Citrix Workspace App
Citrix Workspace app is the easy-to-install client software that provides seamless secure access to everything you need to get work done.
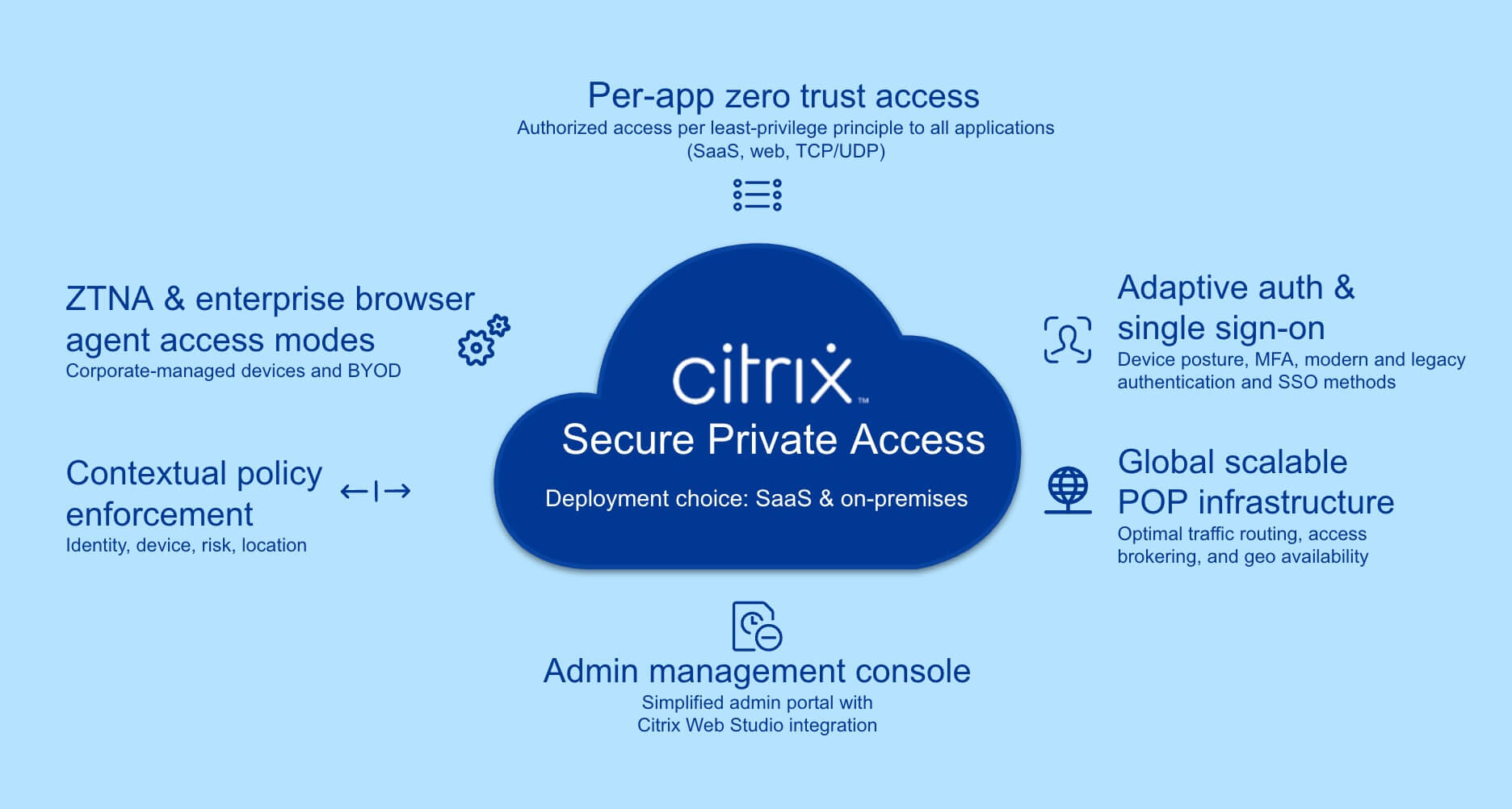
Citrix Secure Private Access provides zero trust network access (ZTNA) to deliver, secure, and manage any application for any user on any device — both managed and unmanaged — on-premises and in the cloud. More secure than a virtual private network (VPN) for protecting corporate data, Citrix Secure Private Access is an ideal VPN replacement. If you use NetScaler® Gateway as a VPN with the Secure Access Client, you can easily roll out ZTNA using the same client for a seamless migration with no impact to your workforce. And because Citrix Secure Private Access is included in the Citrix® platform, you can quickly extend ZTNA to web and SaaS applications — for no extra cost.
VPNs rely on a perimeter-based security model, which is less effective in today's distributed and cloud-based environments. As more resources move outside the traditional network perimeter, VPNs become less effective at protecting these resources, increasing the attack surface. ZTNA is superior to traditional VPNs for remote access security. Unlike VPNs, which grant broad access once a user is authenticated, ZTNA operates on a "never trust, always verify" principle. With ZTNA, access is continuously validated based on user identity and context, significantly reducing the attack surface.
| VPN challenges | ZTNA advantages | |
|---|---|---|
| Attack surface | VPNs use a perimeter security model, provide broad network access, and lack granular controls — all of which open the door to lateral movement within the corporate network by bad actors seeking to exploit other vulnerabilities and gain access to critical systems | ZTNA continuously validates user identity, location, and device and network status before granting access only to specific applications rather than the entire network, which significantly reduces the attack surface and minimizes the chance of an attack spreading across the corporate network |
| Granular access control | VPNs provide access through a secure tunnel, but that access is less restricted, increasing the potential attack surface | ZTNA provides granular access based on user roles and specific application needs so that users only get access to the applications they need, minimizing the risk of lateral movement by attackers |
| Performance | VPNs backhaul traffic through a central data center, which introduces latency that negatively impacts user experience | ZTNA connects users directly to the applications they need without routing traffic through a corporate data center, reducing latency and improving performance |
| Scalability and flexibility | VPNs often rely on legacy infrastructure that can be cumbersome to scale and maintain, especially in a work-from-anywhere scenario | ZTNA is designed to support modern, cloud-based environments and can easily scale to accommodate a growing number of remote user |
| Compliance and governance | VPNs allow broad access, which can make it challenging to meet compliance requirements for HIPAA, GDPR, and PCI-DSS and other regulations, which often mandate strict access controls and least-privilege access | ZTNA limits access to only specific applications and data, which reduces the risk of unauthorized access and helps organizations meet compliance requirements more effectively |
| User experience | VPNs often result in slower connections and can be less user friendly | ZTNA provides a better user experience due to its seamless and direct connections to applications, which affords faster and more reliable access |
| Management | VPNs are time-consuming to manage and maintain and make it challenging to secure endpoints at scale | ZTNA streamlines management with dynamic policy enforcement and enhanced monitoring, minimizing the likelihood of security misconfigurations |
A comprehensive ZTNA solution, Citrix Secure Private Access provides secure, identity-aware access to applications and data in hybrid environments. It uses the zero trust principles of deny-by-default and least-privilege access to ensure that access is continuously verified and contextual, reducing the risk of unauthorized access and data breaches.
Liberate your workers from slow and glitchy VPNs with fast direct access to applications based on their identity
Give your workers the freedom to use their personal devices (bring your own device, or BYOD) to securely access corporate resources in compliance with corporate security policies
Ensure consistent security policies for worker access to applications hosted across on-premises and cloud environments
Before a session is established, Citrix Secure Private Access authenticates a user’s identity using device posture assessment, multi-factor authentication (MFA), and adaptive authentication. This information is then used for contextual application access and single sign-on.
Citrix Secure Private Access integrates with Citrix StoreFront™ — the portal where users access their virtual desktops and applications via single sign-on (SSO) — to enforce access policies at a single point. And, conveniently for users, they can see and access all of their approved applications in Citrix StoreFront, including web and SaaS applications as well the applications they access through VDI.
When a user attempts to access applications or desktops through Citrix StoreFront, Citrix Secure Private Access ensures that the user is authenticated using identity-aware authentication methods for added security, including MFA.
Citrix Secure Private Access uses adaptive authentication methods that can adjust based on the risk profile of the user’s activity. For example, users attempting to access sensitive applications may be required to provide additional verification.
Detailed logging and monitoring help you meet regulatory requirements and improve your overall security posture.
Citrix Secure Private Access uses the zero trust principle of "never trust, always verify" to ensure that access to applications and data is continuously verified. Access policies are dynamically evaluated based on contextual factors like user location, device status, and network trust. For example, access might be restricted or additional authentication might be required if a user connects from an untrusted network.
Citrix Secure Private Access provides flexible options for your secure access needs with both agent-based and agentless options that allow you to balance advanced security with ease of use.
Agent-based access requires installing a client or agent software on the user's device – unless you are already using NetScaler as a VPN. That’s because a NetScaler VPN shares the same agent as Citrix Secure Private Access, so no new installs or upgrades are needed. Agent-based access is best for:
Agentless access provides quick, easy, and flexible access through a secure web browser without compromising basic security requirements and is best for:
Instead of granting broad network access, Citrix Secure Private Access enforces policies that grant access to specific applications. This reduces the attack surface by limiting user access to only the applications that are necessary for the user’s job function.
Application-specific access controls include:
ANALYST REPORT
ZTNA does not need to be expensive or complex to implement. Because the Citrix platform is built with a zero trust architecture that protects all applications — not just VDI — there’s no need to buy additional point solutions to cobble together a ZTNA solution when you already have one.
ZTNA with Citrix Secure Private Access provides:
Routes traffic entirely through your on-premises Citrix environment, making it easier to get security approval because it uses existing approved components
Works seamlessly with modern authentication methods as well as legacy authentication methods like Kerberos and NTLM; supports form-based authentication; and eliminates the need to rewrite authentication protocols for legacy applications
Supports attribute-based identity providers, which is a common use case for M&A
Provides secure access on a per-application basis from cloud VDI to internal applications in a data center or private cloud without using Azure ExpressRoute or any other VPN solution; uses microsegmentation for granular access control to on-premises resources from cloud VDI; and supports single and multi-session VDI
Provides a seamless workflow for admins to configure end-user access permissions for launching web applications in a remote browser in the cloud
Integrates with Citrix StoreFront — a secure portal that uses SSO to enforce access policies at a single point — which conveniently allows users to access all of their approved applications, including web and SaaS applications as well as VDI applications, in one place
Provides a much simpler admin experience because admins can click a button in Citrix Web Studio to access the Citrix Secure Private Access UI to configure access to web and SaaS applications
Makes it easy to pinpoint issues because a single admin portal for management and operations and the use of a single tool, Citrix Director, streamlines help desk triage and the troubleshooting of virtual and private applications
Enables a seamless transition from VPN to ZTNA on an end-user device because NetScaler Gateway (configured as a VPN) and the Citrix Secure Private Access agent are built with the same code base, allowing for a smooth and phased VPN-to-ZTNA migration instead of a forklift approach
Complements secure web gateway (SWG) and cloud access security broker (CASB) controls offered by SASE/SSE vendors for securing external traffic
Provides secure access to all applications — including web and SaaS applications in addition to proprietary applications and VDI applications — on-premises and in the cloud, effectively reducing the complexity of managing multiple ZTNA solutions
Comes included in the Citrix Platform and Universal Hybrid Multi-Cloud License, providing the opportunity for both vendor and cost consolidation
A modern zero-trust security model is preferable to traditional perimeter security, but you can begin implementing zero-trust capabilities in a phased approach while also using a VPN. It’s common to start with ZTNA for unmanaged devices for remote and hybrid employees and contractors as a first step.
Citrix Secure Private Access provides better company data protection and context-based authentication to provide just-enough access rights to employees' required resources. Allowing employees to access private web applications using their preferred browsers improves the user experience. Employees can also access client-server (TCP and UDP) applications without any additional setup by admins, making the access process seamless and hassle free for IT and employees.
Citrix Secure Private Access provides secure and contextual-based access to SaaS and internal web applications through a unified portal or direct link using a native browser. Applications configured with contextual policies will launch in an isolated remote browser to mitigate threats, enforce additional security policies, and protect sensitive data by creating an air gap between the user's device and the application.
Allowing employees, partners, and contractors to use their own devices can pose a security risk. To mitigate this risk, companies deploy VDI in the cloud, isolated from their company networks. After users log on to their cloud desktops, Citrix Secure Private Access automatically establishes a secure connection to the company network, granting the user access to private applications using a zero-trust approach. This robust security measure ensures data security and provides an air gap between the user's device and the company network.
Maintaining and securing company devices can be difficult, especially the devices of remote employees and employees who travel frequently. Citrix Secure Private Access helps IT admins establish a zero-trust-based machine tunnel after the device starts, which allows devices to remain compliant so that company application and data access can be granted.
Before initiating a session, Citrix Secure Private Access verifies a user's identity using single sign-on, device posture assessment, multi-factor authentication (MFA), and adaptive authentication. After establishing a secure session, continuous monitoring ensures adherence to security policies.
Citrix Secure Private Access employs the zero trust principle of "never trust, always verify" to continually validate access to applications and data. Access policies adapt dynamically based on contextual factors such as user location, device status, and network trust. For instance, access may be restricted or additional authentication required if a user connects from an untrusted network.
Citrix Secure Private Access offers flexible choices for secure access with both agent-based and agentless options, providing a balance between advanced security and convenience for the user.
Citrix Secure Private Access enforces policies that provide access to specific applications rather than broad network access. This approach minimizes the attack surface by ensuring that users can only access the applications necessary for their job roles.
RESOURCES