Advanced Persistent Threats (APTs) represent sophisticated, stealthy attacks that can infiltrate and compromise enterprise infrastructures over extended periods. Research suggests that by 2028, the market for advanced persistent threat protection is projected to surpass $23 billion, up from an anticipated $10 billion in 2024.
Given this landscape, it’s crucial to comprehend and address this threat. Let’s explore how Citrix platform safeguards against APTs at each stage:
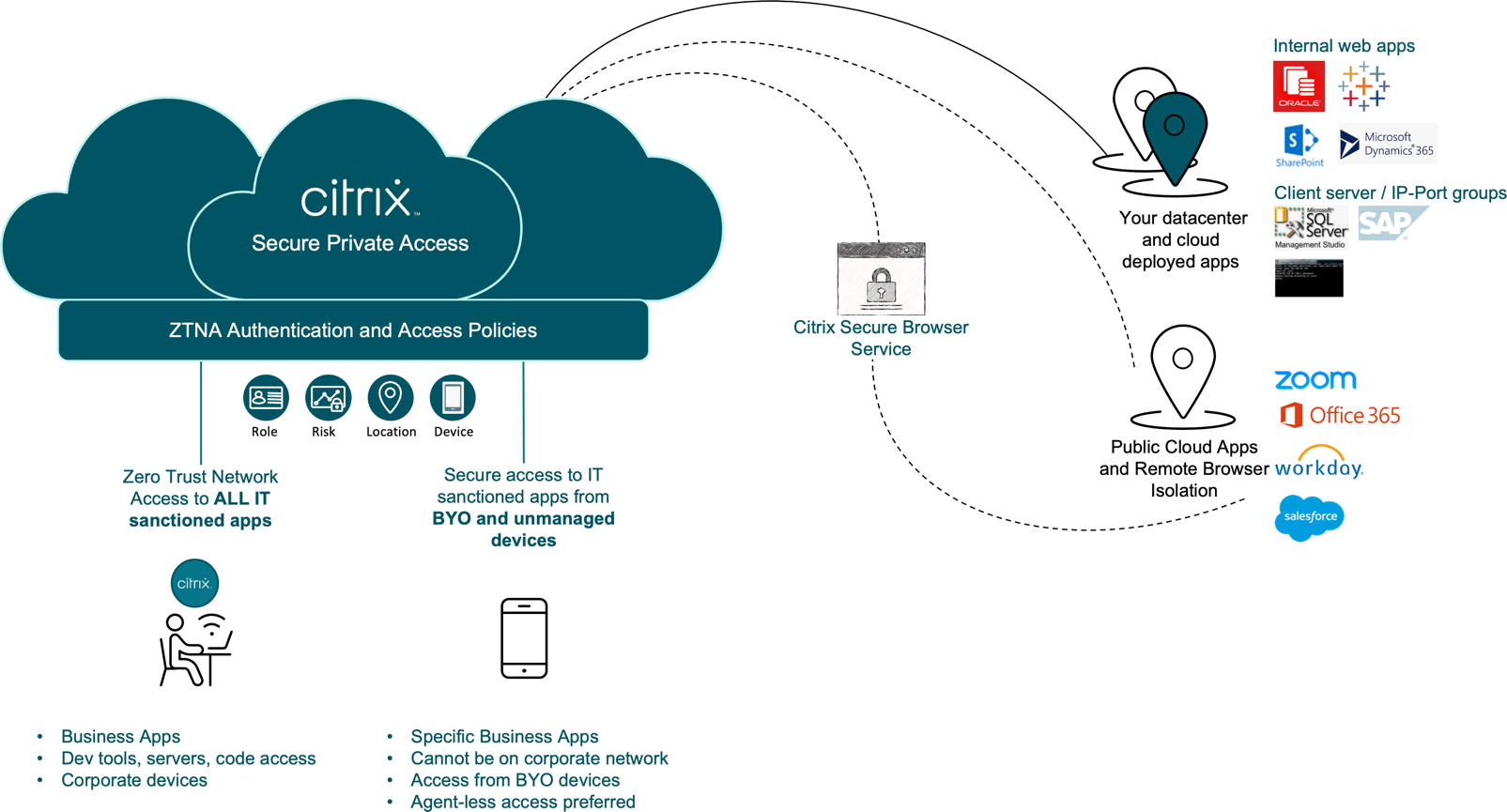
Intrusion: APTs typically begin with intrusion, gaining entry through tactics like spear phishing. Citrix ensures protection by conducting detailed endpoint analysis, enabling anti-phishing software, and employing multi-factor authentication to verify user identities before granting access.
Spread and Exploitation: Malware spreads and exploits vulnerabilities across the enterprise network. Citrix Secure Private Access (SPA) incorporates remote browser isolation, preventing malware from infiltrating the corporate network and restricting lateral movement within it.
Citrix SPA also facilitates real-time monitoring of edge devices, ensuring they are equipped with the latest endpoint protection. Policies can be enforced to restrict access for devices that do not meet specified software and version requirements, safeguarding applications and network integrity.
Survive and Thrive: APTs persist undetected within enterprise networks, coordinating activities like DDoS attacks and data exfiltration. Citrix provides end-to-end visibility across sanctioned applications and users, simplifying monitoring and enabling timely detection of security risks.
Citrix Analytics automates security enforcement based on user behavior and anomalies, reducing manual intervention and mitigating the risk of security breaches.
In essence, Citrix platform offers comprehensive protection against APTs, ensuring businesses remain safeguarded even against evolving and unknown threats.