The number one concern across all of our customers is security. With the average cost of a data breach in 2023 costing over 4.45 million, companies have good reason to invest in their security and zero trust infrastructure. Per Gartner, the top cybersecurity trends in 2023 include threat exposure management and cybersecurity platform consolidation. With the Citrix platform, we’re putting all your secure application delivery tools in one place.
As a crucial part of your application delivery infrastructure, we recognize the key role we play in your zero trust posture. Our zero trust capabilities have grown tremendously in the past year, and we look forward to accelerating our development to get even more features into the hands of customers. Read on to learn more about what key features are a part of our roadmap for 2024.
Citrix Secure Private Access and Citrix Enterprise Browser
Your users access a wide variety of applications and resources from a wide variety of devices and networks. You need to go beyond the traditional security controls of the corporate network to secure that many devices and networks. That’s where Citrix Secure Private Access and Citrix Enterprise Browser help by enabling zero trust network access (ZTNA) to all IT-sanction apps.
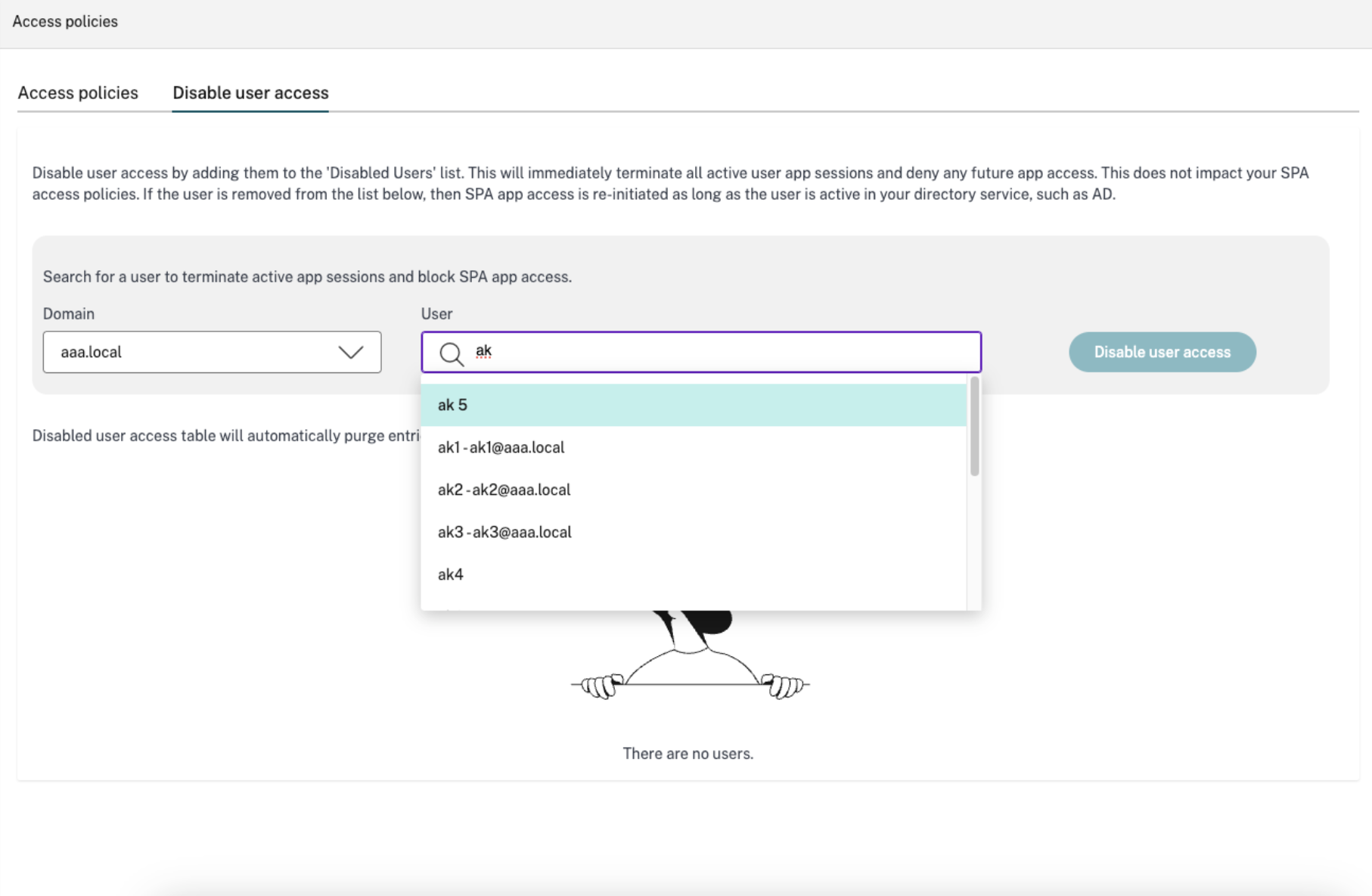
Dynamic revocation of user access
Access security is essential these days, and admins need full access control to manage active Secure Private Access sessions in case of an emergency. For example, if a user’s device is stolen or if any user poses an insider threat, data can be compromised via apps that are accessible. Or, when a user permanently leaves an organization, their active app sessions have to be revoked to secure data. To address scenarios like those described, Secure Private Access now allows admins to immediately terminate all active Secure Private Access sessions for any user. In addition, admins can also add users to a block list to deny any successive app access attempt.
Browser management policies
Companies are looking for a way to allow access to company-owned applications only via a managed browser to ensure the right level of security and data protection. But what if a BYOD strategy is being considered? Citrix Enterprise Browser, a chromium-based browser, can be controlled on company-managed and BYO devices to ensure consistent security and data protection. The Citrix Enterprise Browser enables admins to have comprehensive control over extensions, password saving, developer tools, incognito mode, deleting data on browser exit, data encryption, and more to increase the security posture. Last-mile website security controls like watermark insertion, printing, up/download restriction, and more are available as well. But the story does not stop here! We plan to triple the large number of policies already available to ensure additional management capabilities for the administrator in the coming year.
Citrix Enterprise Browser, an independent solution
Citrix Enterprise Browser is currently installed along with the Citrix Workspace app. As we look to expand our strategy beyond the millions of existing Citrix Workspace app users, admins will now also have the option to install Citrix Enterprise Browser as an independent application for internal web and SaaS app access.
This independent browser is available on Windows and macOS to securely access web and SaaS apps regardless of where they are hosted. You can also configure the Citrix Enterprise Browser as your work or native browser, allowing access to internal links without needing a VPN. Complete management and enhanced security controls protect against malware and other threats on company-managed or BYO devices. The update cycle is aligned to Chromium for the best security and stability. We’re also working on adding support for other platforms for optimal user experiences across different devices.
Enhanced DLP
Browser security is more important than ever! People use browsers to surf the internet and access company data at the same time. Bad actors often compromise legitimate internet sites to infect user devices with malware to steal company data. To prevent such data exfiltration, Data Loss Prevention (DLP) capabilities like clipboard containers, data encryption, customizable watermarks, PII masking, or granular file control management can help. Citrix Enterprise Browser delivers all these protection mechanisms and more to keep your data secure.
Device Posture
Your users access company resources from an ever-increasing number of endpoints and locations. You need to ensure they’re doing so safely. That’s where Device Posture comes in. This solution checks end devices for compliance before allowing access to company resources. We plan to bring even more capabilities to Device Posture to strengthen your security before users even log on, so your data stays secure no matter what devices your employees use.
Generic and Vendor Specific Antivirus and Browser Checks
Securing application access is critical to protecting company infrastructure and data from malware infection or theft. Checking the user’s device status is crucial before allowing application access. But basic checks like OS updates or running services are no longer accurate. Deeper checks are needed to apply the right level of security.
For example, accessing your enterprise applications from a browser is a popular use case. Ensuring the browser used to access is secure, Device Posture Service allows customers to specify parameters like browser vendor, build, version, and authenticity as a condition for browser-based access, thereby ensuring only compliant browsers are used. Allowing file access or transfer also requires the capability to check the antivirus status against the latest viruses on the market. Checks like the last device scan time, antivirus version, vendor/software, virus definition updates, and more are available in Device Posture Service. Based on the scan result, contextual application access is enforced for the user.
Test mode
When putting Device Posture configurations into production without testing, user access may be denied. In the worst case scenario, users can lose application connectivity or have their access restricted without knowing why, resulting in an increased number of helpdesk tickets and user frustration. The new Test Mode feature allows admins to collect endpoint data and plan a rollout accordingly before enforcing access control.
Skip check
Companies using Device Posture checks and allowing access to contractors or partners often struggle with access denied for non-company-owned devices. Also, company-managed devices offline for a longer time can run into the same problem due to outdated agents. Device Posture Service enables admins to create a customized warning message with the option to install/update the agent or skip the device scan. Users skipping the device scan are granted limited access along with additional security controls enabled. Device Posture Service allows for the least privileged access to company resources in any scenario.
HDX
HDX is one of the core components of the Citrix platform. With its industry-leading end user experience, based on adaptive technologies and de-duplication, there are clear reasons to use HDX. But HDX isn’t just an end user experience booster. Citrix HDX allows IT to support anytime, anywhere work while maintaining a high level of security and control over corporate data.
Secure HDX
Security has always been one of the biggest strengths of our ICA protocol. Now we’re making it even stronger with Secure HDX, a replacement for Secure ICA.
Secure HDX provides true end-to-end application level encryption, regardless of the network level encryption for the connection. It uses AES 256 in GCM mode, a leap forward from the RC5 128-bit encryption used by Secure ICA. Secure HDX enables administrators to maintain their data in transit securely, even when they don’t have control over the network in use. This prevents bad actors and intermediary devices from looking at your data, even our own NetScaler Gateway and Gateway Service.
Session Recording
Many industries must maintain data security for regulatory requirements – such as healthcare and finance. Session Recording allows organizations to record on-screen user activity for applications that deal with sensitive information, monitoring, and preventing the leakage of sensitive information from virtual sessions. We are bringing even more features to Session Recording so you can monitor the data flow in your environment granularly.
Export event logging
Session Recording is an important data source for the Citrix platform. It allows you to capture system events such as file transfers and USB device connections. Other Citrix services can ingest and consume events from Session Recording, like Security Analytics.
A big piece of feedback we’ve gotten from customers is that they use additional SIEM platforms, and want to see Session Recording events there as well. We are working on providing a way to allow customers to export events to 3rd party SIEM platforms of their choice. Initially, we are focusing on compatibility with Splunk and Microsoft Sentinel.
Session Recording for web and SaaS applications
These days, users aren’t just accessing traditional virtual apps and desktops, they are also using web and SaaS apps to get critical work done. Zero trust access is crucial for a hybrid working environment, and Secure Private Access provides an ideal solution for Web applications and SaaS use cases.
Although Secure Private Access itself has many security features, it does not provide insights into user behavior while the applications are open. In Citrix Virtual Apps and Desktops and Citrix DaaS, Session Recording plays an important role in security, compliance, and troubleshooting. We are planning on bringing these same functionalities to Secure Private Access as well.
Citrix Features Explained: Session Recording with Citrix DaaS
Printing job insights
Security in the hybrid workplace is a big challenge. If your employees need to print, they need to connect to external devices like printers. However, bad actors can use those devices to access sensitive business data. You need a way to protect those essential devices from internal and external threats.
That’s where printing job insights comes in. Session Recording can provides insider threat management capabilities due to its event detection and response functionality. To start, we are focusing on printing job insights. Often end users need to be able to print as part of their daily workflows but you need to be able to keep track of behavior and investigate outliers. With this functionality, you will be able to track and take action on any irregular printing behavior to protect your data.
Learn More
We are looking forward to bringing you these exciting developments throughout 2024. Stay up to date with our latest releases via updates.cloud.com – which now tracks on-premises releases as well! As always, you can learn more about our existing features on product documentation.
To learn more about the Citrix platform, visit our website.
Disclaimer: This publication may include references to the planned testing, release and/or availability of Cloud Software Group, Inc. products and services. The information provided in this publication is for informational purposes only, its contents are subject to change without notice, and it should not be relied on in making a purchasing decision. The information is not a commitment, promise or legal obligation to deliver any material, code, or functionality. The development, release, and timing of any features or functionality described for products remains at the sole discretion of Cloud Software Group, Inc.