In an era of relentless digitization, where the boundaries between personal and professional realms blur with technological advancements, security stands as an ever-pressing concern. Managing credentials across numerous apps and platforms poses a significant challenge, especially considering the common practice of reusing or slightly altering passwords. The consequences of credential exposure extend beyond personal inconvenience to potentially compromising corporate infrastructures. In this article, we delve into how Citrix technology offers robust solutions to mitigate these risks, ensuring a secure digital environment.
Understanding Account Take Over (ATO)
Account Takeover (ATO) occurs when cybercriminals gain control of online accounts using pilfered usernames and passwords. These credentials are often acquired from data breaches, social engineering, or phishing attacks and are traded in underground markets. Cybercriminals employ automated bots to exploit these credentials across various online services, ranging from retail and finance to social media platforms, in a bid to gain unauthorized access.
Common Methods of Credential Theft
Credential theft can be orchestrated through various means, including screen capture, keyloggers, and malware installation. These techniques underscore the critical importance of implementing robust security measures to safeguard sensitive information.
Mitigating ATO Risks with Citrix Technology
Citrix offers two key solutions designed to mitigate the risks associated with ATO:
- Citrix Enterprise Browser:
- Provides secure, identity-aware access to browser-based applications without the need for a VPN.
- Enforces granular controls for data loss prevention and threat mitigation, ensuring “just enough” access.
- Utilizes a zero-trust approach to authentication, allowing secure access regardless of user location, device, or risk profile.
- Incorporates contextual security policies such as anti-screen sharing, anti-keylogging, and data watermarking to prevent credential leakage.
- Enables administrators to customize security policies, control browser-level settings, and manage access to password managers and developer tools.
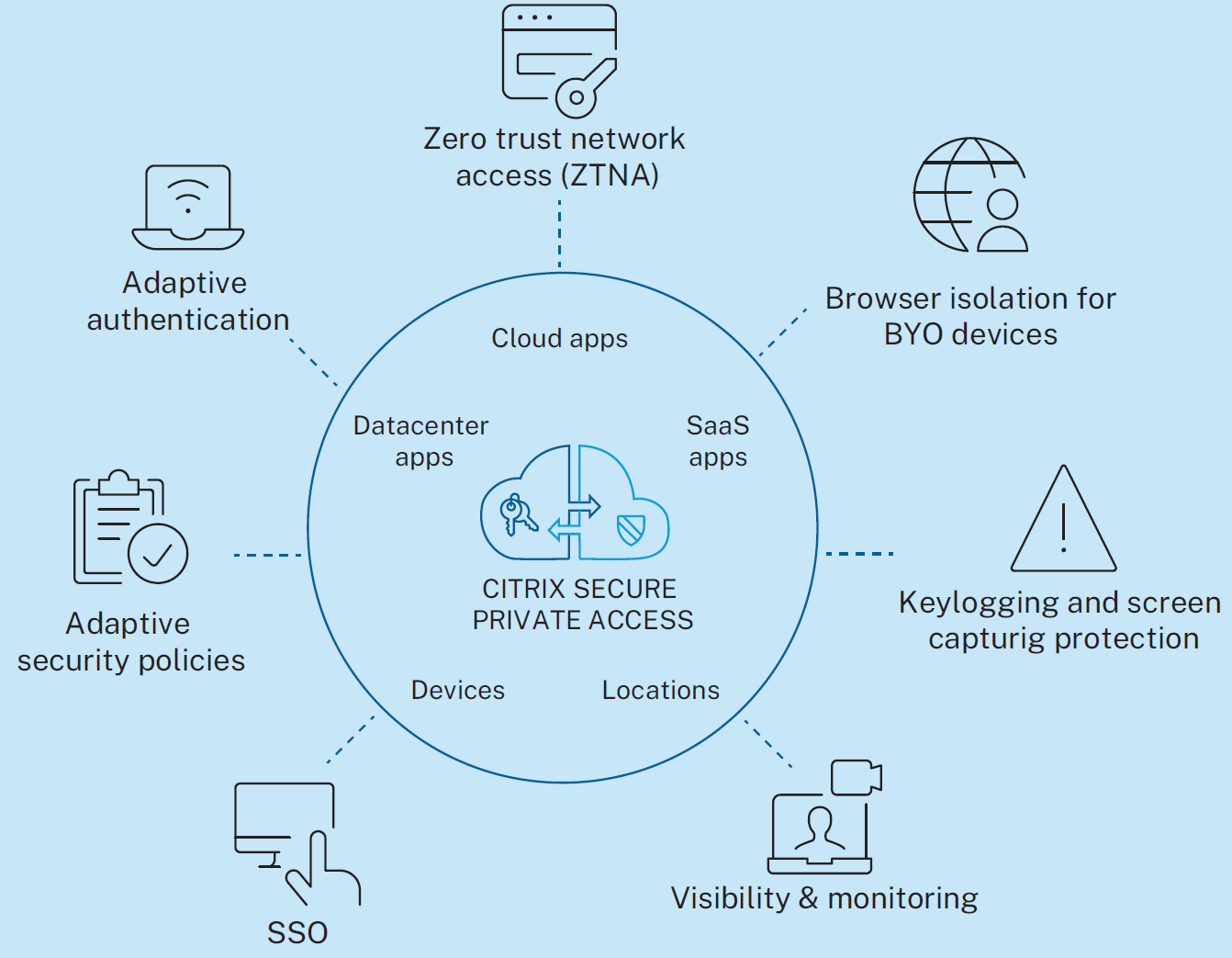
- Citrix Secure Private Access (SPA):
- Delivers Zero Trust Network Access (ZTNA) for all IT-sanctioned applications, re-establishing trust at each interaction.
- Implements adaptive access and security controls to enforce contextual security, making it challenging for attackers to replicate user contexts.
- Offers browser isolation to navigate the web securely, minimizing the impact of potential breaches on corporate environments.
Conclusion: Enhancing Digital Security with Citrix Solutions
By leveraging Citrix Enterprise Browser and Citrix Secure Private Access, organizations can empower their employees to access corporate networks and personal apps seamlessly while mitigating the risks of credential leakage and ATO. These solutions not only ensure robust security but also contribute to a better quality of life by offering freedom and flexibility in accessing digital resources.
Stay tuned for more insights on leveraging Citrix technology to address evolving security challenges in our upcoming blog articles.
Connect with Kumar Palaniappan on LinkedIn.
Disclaimer: This publication may include references to the planned testing, release and/or availability of Cloud Software Group, Inc. products and services. The information provided in this publication is for informational purposes only, its contents are subject to change without notice, and it should not be relied on in making a purchasing decision. The information is not a commitment, promise or legal obligation to deliver any material, code, or functionality. The development, release, and timing of any features or functionality described for products remains at the sole discretion of Cloud Software Group, Inc.