Outlook Web Access is often used to provide remote mail access to users via a web interface. Citrix NetScaler can be used to reverse proxy connections to provide secure remote access and also provide Single-Sign-On to OWA as outlined in the article here: http://support.citrix.com/article/CTX128197 . Jeff Sani has also blogged about it and shared a very helpful configuration script here: http://www.jeffsani.com/downloads/owa_attachment_config.txt.
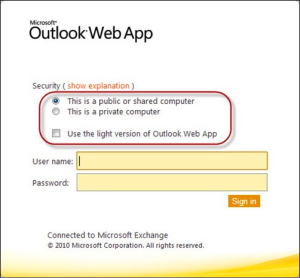
Microsoft provides some options to login as a public or private computer and whether or not to force the light version of OWA as shown in the screenshot below:
Microsoft pushes some parameters when users login selecting these options and you can force these selections even when Single-Sign-On is performed by the NetScaler using the AAA-TM feature. The parameters are outlined here:
- flags=0&trusted=0 –> public computer, full client
- flags=4&trusted=4 –> private computer, full client
- flags=5&trusted=4 –> private computer, lite client
- flags=5&trusted=0 –> public computer, lite client
Note regarding parameters for light version:
Several times, the flags parameter needs to be changed to flags=1 to force the light version of OWA instead of flags=5 used here.
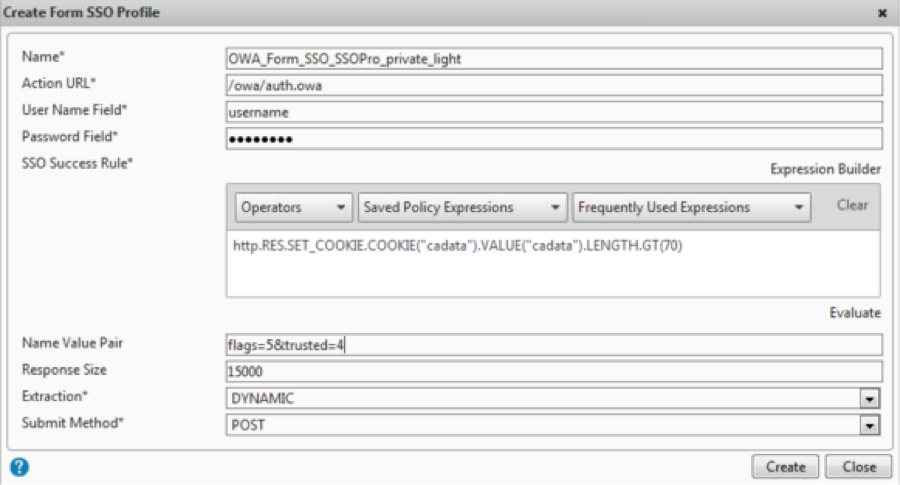
Some organizations like to force these parameters by configuring the NameValue pair parameter on a FormSSO profile depending on the user’s group membership and applying a traffic management policy to apply the FormSSO profile pertaining to the specific LDAP group.
For example, if a user belonging to the “Contractors” group is trying to login to OWA remotely, then the traffic management policy can be setup to look for the user’s group membership and if the user belongs to the “Contractors” group in LDAP, then it forces the login selections to be “public” and “light”. Admins can do the same to restrict iPads and iPhones to only login with “public” and “light” parameters. The enforcing of the parameters can be done at FormSSO profiles as will be later shown in this blog.
If the organization’s internal policies dictate that the end users should see the login options, then the following procedure outlines the configuration and customization that can be done at the NetScaler to provide those selections.
Customization on tmindex.html page
- Download tmindex.html to the computer. Note: Ensure that you back up this original file.
- Open the file for editing with preferred document editor software.
- Locate the following section of text. The line where this section is located will vary depending on the version of NetScaler:
<!– Logon box –>
<tr>
<td class=”carbonBoxBottom” valign=”bottom”>
<script language=”javascript” type=”text/javascript”>
documentWriteGlowBoxUpper();
</script>
- Insert the following text immediately after the section described in step 3 :
<SCRIPT type=”text/javascript”>
function getCookie(name) { // use: getCookie(“name”);
var re = new RegExp(name + “=([^;]+)”);
var value = re.exec(document.cookie);
return (value != null) ? unescape(value[1]) : null;
}
var today = new Date();
var expiry = new Date(today.getTime() + 28 * 24 * 3600 * 1000); // plus 28 days
var expired = new Date(today.getTime() – 24 * 3600 * 1000); // less 24 hours
function setCookie(name, value) { // use: setCookie(“name”, value);
document.cookie=name + “=” + escape(value) + “; path=/; expires=” + expiry.toGMTString();
}
function storeValues(form) {
setCookie(“publicprivate”, form.publicprivate.value);
setCookie(“lightfull”, form.lightfull.value);
return true;
}
</SCRIPT>
- The next two lines should read as follows:
<FORM method=”post” action=”/cgi/login” name=”vpnForm” autocomplete=”off” style=”margin:0″
onSubmit=”clean_name_cookie(this);”>
Insert the following string into the onSubmit tag: storeValues(this);”
The HTML code should now read as follows:
<FORM method=”post” action=”/cgi/login” name=”vpnForm” autocomplete=”off” style=”margin:0″
onSubmit=”return storeValues(this); clean_name_cookie(this);”>
Creating the Drop-Down Menu
To create a drop-down menu, complete the following procedure:
- On the same index,html page, locate the following line:
<SCRIPT language=JavaScript>ns_showpwd();</SCRIPT>
- Add the following line immediately after the preceding line:
<TR>
<TD align=center><SPAN style=”padding-right:10px;”>Domain:</SPAN></TD>
<TD>
<select name=”publicprivate” size=”1″ style=”width: 100px;”>
<option value=”public”>public</option>
<option value=”private”>private</option>
</select>
<select name=”lightfull” size=”1″ style=”width: 100px;”>
<option value=”light”>light</option>
<option value=”full”>full</option>
</select>
</TD>
</TR>
- Save the changes and copy the file to the /netscaler/ns_gui/vpn directory and test by connecting with a client to the Access Gateway virtual server.
Creating a Procedure to Ensure that the Custom Page Endures a Restart
To create a procedure to ensure that the custom page endures a restart, complete the following tasks:
- Connect to the appliance using an SSH client such as PuTTY.
- Type shell.
- Create a directory on the hard drive to save the custom file:
mkdir /var/customizations - Run the following command to copy the modified page to the new directory:
cp /netscaler/ns_gui/vpn/tmindex.html /var/customizations/ - Create a startup script file called rc.netscaler in the /nsconfig directory if it does not exist:
cd /nsconfig
touch rc.netscaler - Run the following command to copy the copy command to the rc.netscaler file:
echo cp /var/customizations/index.html /netscaler/ns_gui/vpn/index.html >> /nsconfig/rc.netscaler
Traffic Management SSO Profiles/Policies:
Public and Full:
add tm formSSOAction OWA_Form_SSO_SSOPro_public_full -actionURL “/owa/auth.owa” -userField username -passwdField password -ssoSuccessRule “http.RES.SET_COOKIE.COOKIE(\”cadata\”).VALUE(\”cadata\”).LENGTH.GT(70)” -nameValuePair “flags=0&trusted=0” -responsesize 15000 -submitMethod POST
add tm trafficAction OWA_2010_Prof_trusted_full -appTimeout 1 -SSO ON -formSSOAction OWA_Form_SSO_SSOPro_public_full
add tm trafficPolicy owa2k10_pol_public_full “HTTP.REQ.URL.CONTAINS(\”owa/auth/logon.aspx\”)&& HTTP.REQ.COOKIE.CONTAINS(\”public\”)\”)&& HTTP.REQ.COOKIE.CONTAINS(\”full\”)” OWA_2010_Prof_public_full
Private and Full:
add tm formSSOAction OWA_Form_SSO_SSOPro_private_full -actionURL “/owa/auth.owa” -userField username -passwdField password -ssoSuccessRule “http.RES.SET_COOKIE.COOKIE(\”cadata\”).VALUE(\”cadata\”).LENGTH.GT(70)” -nameValuePair “flags=4&trusted=4” -responsesize 15000 -submitMethod POST
add tm trafficAction OWA_2010_Prof_trusted_full -appTimeout 1 -SSO ON -formSSOAction OWA_Form_SSO_SSOPro_private_full
add tm trafficPolicy owa2k10_pol_private_full “HTTP.REQ.URL.CONTAINS(\”owa/auth/logon.aspx\”)&& HTTP.REQ.COOKIE.CONTAINS(\”private\”)\”)&& HTTP.REQ.COOKIE.CONTAINS(\”full\”)” OWA_2010_Prof_private_full
Private and Light:
add tm formSSOAction OWA_Form_SSO_SSOPro_private_light -actionURL “/owa/auth.owa” -userField username -passwdField password -ssoSuccessRule “http.RES.SET_COOKIE.COOKIE(\”cadata\”).VALUE(\”cadata\”).LENGTH.GT(70)” -nameValuePair “flags=5&trusted=4” -responsesize 15000 -submitMethod POST
add tm trafficAction OWA_2010_Prof_trusted_full -appTimeout 1 -SSO ON -formSSOAction OWA_Form_SSO_SSOPro_private_light
add tm trafficPolicy owa2k10_pol_private_full “HTTP.REQ.URL.CONTAINS(\”owa/auth/logon.aspx\”)&& HTTP.REQ.COOKIE.CONTAINS(\”private\”)\”)&& HTTP.REQ.COOKIE.CONTAINS(\”light\”)” OWA_2010_Prof_private_light
Public and Light:
add tm formSSOAction OWA_Form_SSO_SSOPro_public_light -actionURL “/owa/auth.owa” -userField username -passwdField password -ssoSuccessRule “http.RES.SET_COOKIE.COOKIE(\”cadata\”).VALUE(\”cadata\”).LENGTH.GT(70)” -nameValuePair “flags=5&trusted=0” -responsesize 15000 -submitMethod POST
add tm trafficAction OWA_2010_Prof_trusted_full -appTimeout 1 -SSO ON -formSSOAction OWA_Form_SSO_SSOPro_public_light
add tm trafficPolicy owa2k10_pol_public_light “HTTP.REQ.URL.CONTAINS(\”owa/auth/logon.aspx\”)&& HTTP.REQ.COOKIE.CONTAINS(\”public\”)\”)&& HTTP.REQ.COOKIE.CONTAINS(\”light\”)” OWA_2010_Prof_public_light
Note regarding customization options:
Please note that the customization outlined here only depicts selection based on a dropdown. Admins can choose to exactly imitate the selection options as radio buttons and checkboxes and create cookie values according to the selections by only slightly modifying the HTML code shown here.
Example for alternate way to create cookies using radio buttons and checkboxes instead of drop-downs:
?>
<tr>
<td colspan=2 >
<label for=”text”>Security</label>
<input type=”radio” name=publicprivate value=”public” checked> This is a public or shared computer<br>
<input type=”radio” name=publicprivate value=”private”> This is a private computer
</td>
</tr>
<tr>
<td colspan=2 >
<label for=”text”>Light Version?</label>
<input type=”checkbox” name=lightversion value=”light”> Use the light version of Outlook Web App
</td>
</tr>
<?
In this case, the traffic management policies might need to be revisited and modified to look for the right values created in the HTML code above.
This article only intends to highlight the capability of the NS in being able to provide the same selection options as the built-in OWA login page.