Overview
The most popular phrase of each and every consultant is “it depends” – we like this phrase and we use it a lot J
However, the fact that you can say “it depends” doesn’t make you a good consultant of course – if consultant cannot give you any straight answers, he is kind of useless. Even though we usually say “it depends”, most of the time there are answers that will be correct in majority of the cases.
Some design decisions are usually preferred and some are considered exceptions. Never trust consultant that always recommends the same solution for different issues and environments – “one size fits all” solution typically means that solution is not mature enough and optimized for different scenarios (that’s why I love our FlexCast – it can be really tailored based on customer needs).
Provisioning Services can be described as single-image solution that can also offload the read IOPS from your storage (read-cache appliance sitting between your VM and storage).
When to use persistent store
In theory, this is perfect solution – one to many, you’ve to manage only single image, all issues can be easily solved just by rebooting the machine. But what if you run into some showstoppers – for example one of your mission critical applications requires persistent data and doesn’t work in read-only mode?
When do you want to make your data persistent?
- Applications that requires persistent storage – typically applications that will automatically generate machine-specific ID somewhere in configuration files – SCCM, antivirus…
- Historical data that you want to keep for auditing and\or troubleshooting – typically various log files
- Improving overall performance – sometimes, keeping data persistent can improve your performance –for example redirection of page file and any frequently updates files (especially if they don’t use delta updates)
- Special requirements – one of examples can be the license grace period or application streaming cache. Or applications with first run penalty
- Security – there is a potential gap in security when you reset your computer to default state before it will download all updates\check all requirements – similar to boot time protection of Windows Firewall, you may want to keep such data persistent
How to enable it
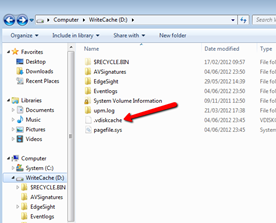
When you select “Cache on Target Device Hard Drive” option, new drive is automatically mapped for each provisioned machine. On this drive, you can find two important parts – write cache file itself and the rest of the drive. On reboot, only write cache file (.vdiskcache) is reset to default state, while the rest of the drive is persistent.
Example write cache drive
As you can see, persistent drive is just a regular drive and doesn’t require any special handling – it’s NOT HSM or interception\redirection (like application isolation or Personal vDisk).
One disadvantage is that you cannot use any built-in rules to specify which data are persistent and which are not.
So how can you redirect files\folders and make them persistent?
How to use it 1 – configuration change
The first one is rather simple and highly depends on what you want to redirect – simply change the location during installation or change it in the configuration. For example follow these simple steps to redirect your event log files. Same principle applies to most of the applications – if there is any setting where you can change the location, use it.
But what if your application is hardcoded and you don’t have an option to redirect it? Another option is to use the tools that are provided by underlying operating system and specifically file system.
How to use it 2 – core file system functionality
Since Windows 2000, Microsoft supports so called junction points. NTFS junction point is NTFS functionality that allows you to seamlessly redirect one folder into another. Technically, junction points are just implementation of reparse points – which contains special instructions (user data) that are automatically processed by file system driver (so reparse point stores user data + tag to identify which driver should process them). Long story short, this is processed on a low level and your application doesn’t need to specifically support reparse point to benefit from them.
System32 redirected to temporary directory (EXAMPLE)
Junction points are extremely powerful when used properly – I’ve used them many, many times to fix an issues with application that was using hardcoded paths – for example if I wanted to install my application to D:\ ABC and application ABC used hardcoded C:\ABC, I simply installed to my folder and then created junction C:\ABC <==> D:\ABC.
Since Windows Vista\2008, full symlinks were introduced. While junction points can only link to directories on a local volume, symlinks are much more powerful and actually supports all 4 R(emote) and L(ocal) scenarios – L2L, L2R, R2R and R2L (so you can map your network share to your local folder).
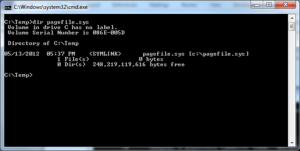
Another great benefit of symlinks is that you can use it to redirect files (and not only folders).
Pagefile.sys redirected to temporary directory (EXAMPLE)
So if you need to redirect only single file, you don’t need to redirect whole folder (typically configuration file that are bound to specific machine).
Registry settings are more complicated of course – usually I recommend implementing simple startup\shutdown scripts (why not logon scripts? Read my previous blog post).
In very rare cases, you cannot use them – in that case solution is a bit more complicated and I don’t want to go into technical discussion (as it would be article on its own), but generally you need to do following:
1.) Mount hive during startup
2.) Implement your registry settings in this custom hive file
3.) Implement REG_LINK registry type to redirect the data
But be careful
When designing persistency exceptions, you should be very careful (and consult with CCS whenever possible).
First of all, persistent data is something that goes against the idea of single image management. Persistent data adds some uniqueness to each of the provisioned machines and makes it harder for troubleshooting – and if not designed properly, can even decrease the performance over time.
Also don’t forget that there is a penalty – storage requirements, since you will need to store persistent data.
Martin Zugec
Principal Consultant